
Cyber Security Mesh
Your data is your power, and it needs to be protected
How can you be confident that your IT system or a particular application is protected from online threats?
Since no two IT infrastructures are alike, the most potent cyberthreats are created specifically to target each organization's unique weaknesses. Regular security assessments guarantee compliance with industry best practices and provide you a comprehensive knowledge of your security posture.
Cyber Security Services
Security Assessment

Penetration Testing
An adversary simulation that is powered by threat intelligence shows potential attack paths and gives you a general idea of your security posture from the attacker's point of view.
Payment Systems Security Assessment
A thorough examination of the hardware and software components of various payment systems is performed to identify any vulnerabilities or potential fraud situations.
Transportation Systems Security Assessment
Specialized research focused on identifying security problems related to mission-critical components of modern transportation infrastructure from Automotive to Aerospace.
Application Security Assessment
A complete investigation of any program, including huge cloud-based solutions, embedded software, and mobile apps, for implementation faults and business logic bugs.
ICS Security Assessment
Insight into the current attack surface and the related economic effect of possible assaults is provided by case-specific threat modeling, vulnerability assessments, and Industrial Control Systems and their constituent parts.
Smart Technologies and IoT Security Assessment
Detailed evaluation of modern highly-interconnected devices and their backend infrastructure, revealing vulnerabilities on firmware, network, and application layers.
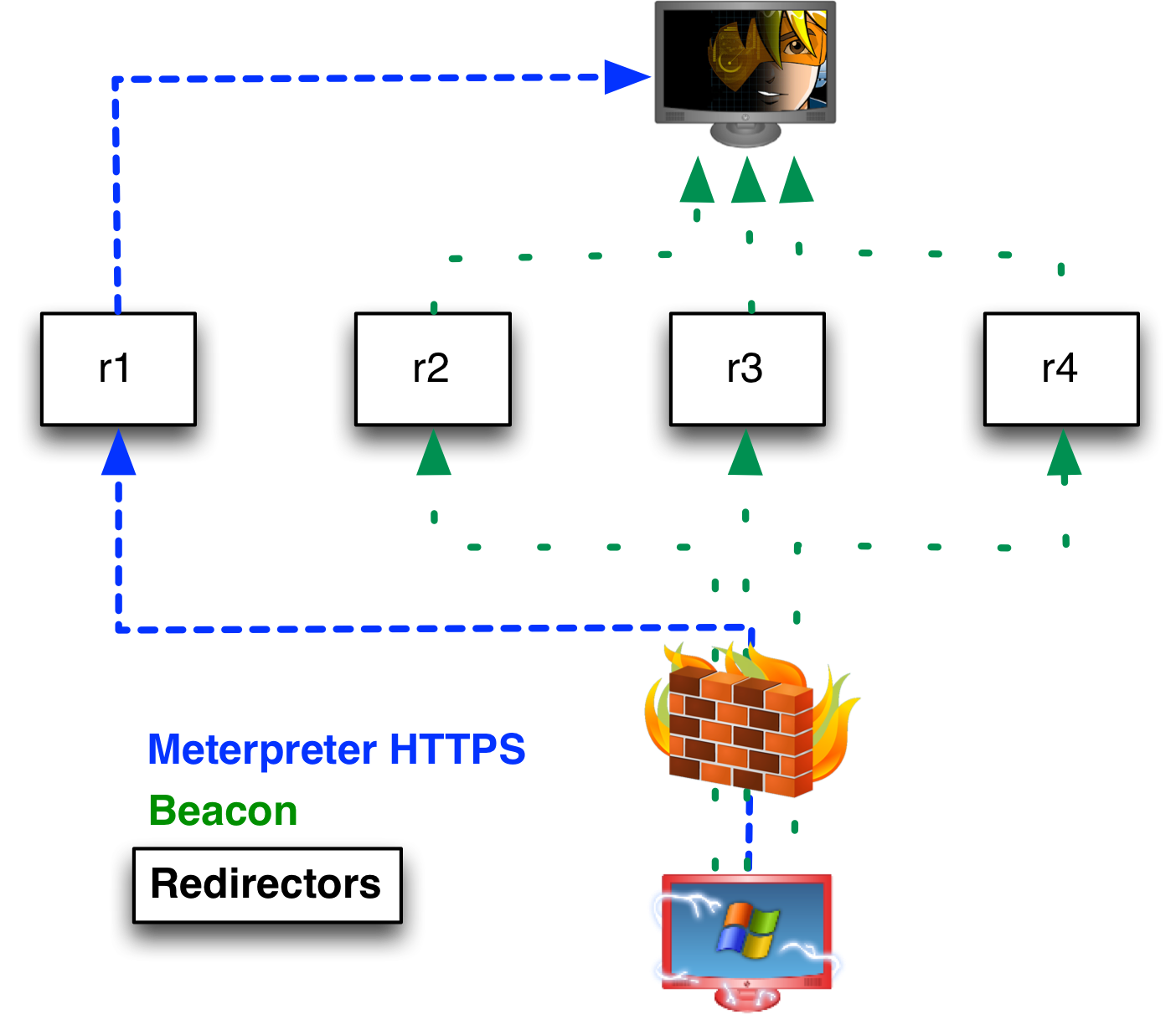
Red Teaming
Threat Intelligence-driven adversary simulation helping to evaluate the effectiveness of your security monitoring capabilities and incident response procedures.
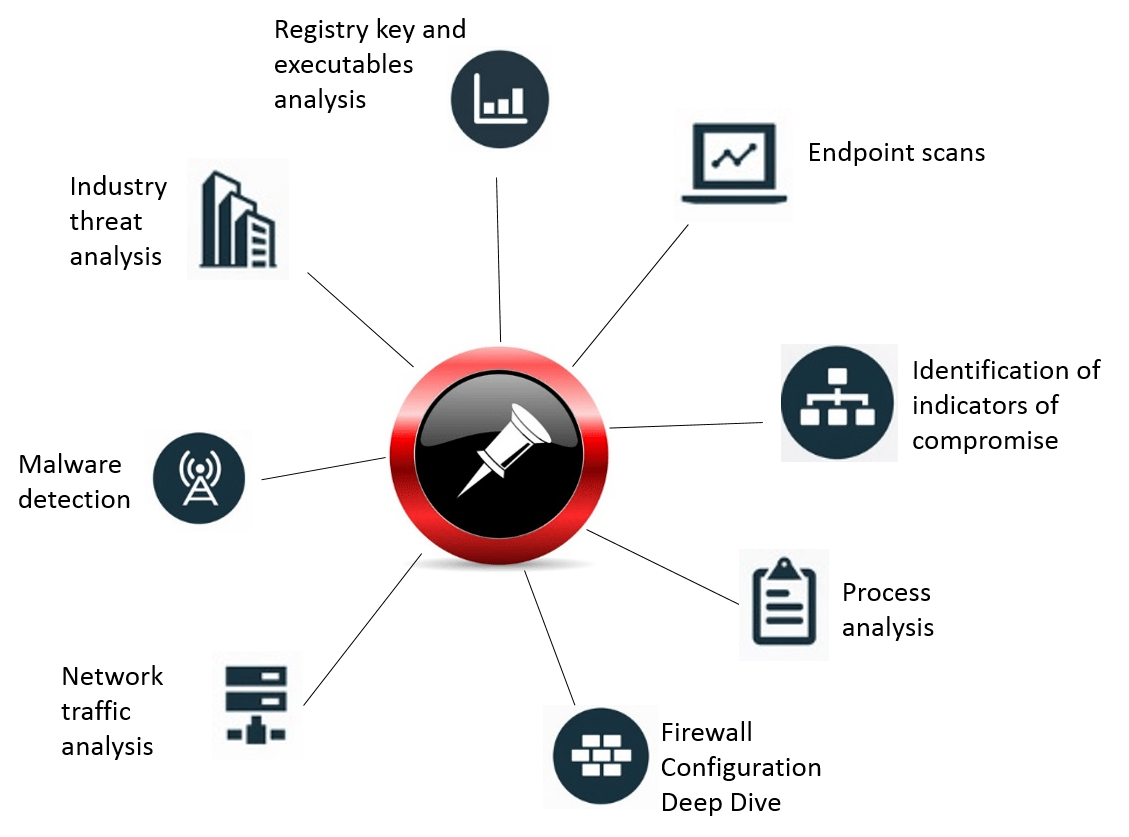
Compromise Assessment
Comprehensive analysis uses a variety of techniques, including as threat intelligence, vulnerability analysis, and incident investigation, to find penetration attempts.
Proactive mitigation
Timely identification of security incidents mitigates their impact before it becomes apparent and protects your resources from similar attacks in future.
